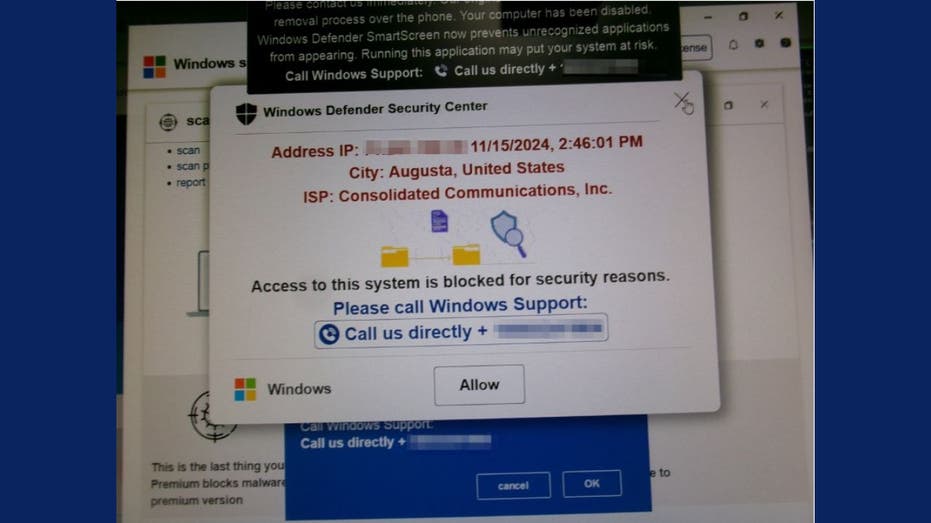
Windows Defender Security Center Scam: Safeguard Your Computer Against Deceptive Pop-Ups
In the digital age, scams are becoming increasingly sophisticated. A recent email from a reader, Janet D., sheds light on a troubling experience that many users could face. Here’s her story.
Janet Recalls Her Scary Encounter
“I received a pop-up that froze my computer and read, ‘Access to this system is blocked for security reasons’ from Windows Defender Security Center,” Janet shared. The pop-up was alarming, accompanied by an audio message and a siren, creating an atmosphere of panic.
In her moment of distress, Janet made the mistake of calling the number displayed on her screen. Following the scammer’s instructions, she pressed Ctrl + Shift + Esc, which unblocked her computer. However, the scammer then persuaded her to download software from UltraViewer.net, a legitimate tool that is frequently misused by scammers.
Understanding the Scam
Recognizing the tactics used by scammers can help you avoid falling victim to these schemes. Here are the common elements to be aware of:
Unsolicited Pop-Ups: Janet’s experience is a textbook example of a common scam method. Fake alerts that appear to be from Microsoft or other security services are designed to panic users. Remember, legitimate companies do not issue pop-ups with support numbers or direct you to download software.
Urgent Visual and Audio Cues: Scammers often employ alarming sounds and flashing messages to create a sense of urgency, pushing victims to act without thinking critically.
Requests for Remote Access Software: Scammers frequently ask users to download remote access tools, such as UltraViewer or TeamViewer. While these tools can be useful for legitimate tech support, downloading them at the request of an unknown caller is a major red flag.
What to Do If You Encounter a Scam
If you encounter a suspicious pop-up, it’s crucial to remain calm and follow these steps:
1. **Do Not Engage**: Avoid calling the displayed number or following any on-screen instructions. Instead, independently verify any suspicious messages or phone numbers.
2. **Use Task Manager**: Press Ctrl + Alt + Del to open the Task Manager and close the browser or application showing the scam message.
3. **Assess the Situation**: Scammers thrive on urgency. Take a moment to evaluate your options before making any decisions.
4. **Uninstall Any Suspicious Software**: If you downloaded UltraViewer or any similar applications, remove them immediately.
5. **Update Your Passwords**: Change passwords for critical accounts, especially for email and banking. Consider using a password manager for enhanced security.
6. **Enable Two-Factor Authentication**: This extra layer of security can help protect your accounts even if someone obtains your login details.
7. **Consult a Professional**: If you suspect your computer is compromised, seek help from a tech professional or contact Microsoft Support.
Understanding the Limitations of Antivirus Software
Janet also pointed out that her antivirus software did not flag the scam. This highlights a crucial point: many scams rely on social engineering rather than malware, making them harder for antivirus programs to detect. Regular system scans can help identify hidden threats, but being aware of human psychology is equally important.
Actions to Take After a Scam Encounter
If you’ve interacted with a scammer, take these precautionary steps:
1. **Cease Communication**: Stop all interactions with the scammer immediately.
2. **Report the Scam**: Notify your local law enforcement agency or cybercrime unit and provide details about the scam.
3. **Contact Financial Institutions**: If you shared any financial information, inform your bank and credit card companies for advice on securing your accounts.
4. **Monitor Your Accounts**: Keep a close watch on your bank and credit card statements for any unauthorized transactions.
5. **Notify Credit Bureaus**: Consider placing a fraud alert with credit reporting agencies to prevent new accounts from being opened in your name.
6. **Be Cautious of Future Communications**: Remain vigilant about any unsolicited messages or calls, as scammers may attempt to target you again.
7. **Consider Identity Theft Protection**: If your personal information has been compromised, look into identity theft protection services that can guide you through reporting and recovery, often including identity theft insurance.
Conclusion: Stay Vigilant and Informed
Janet’s experience serves as a reminder that even the most cautious individuals can fall victim to cleverly crafted scams that exploit fear and urgency. By recognizing warning signs like unsolicited pop-ups, high-pressure tactics, and requests for remote access, you can protect yourself and your personal information.
If you ever find yourself in a situation similar to Janet’s, remember to stay calm, verify the legitimacy of any alerts, and take proactive steps to secure your system. Scammers depend on quick reactions; slowing down and staying in control is your best defense.
Have you encountered any new scams that others should be aware of? Share your experiences with us.
For more tech tips and security alerts, consider subscribing to our newsletter. Stay informed and protect yourself against potential threats.

