Is Your iPhone App Spying on You? Discover the Insights from Apple’s App Privacy Report
Apple’s App Privacy Report is a groundbreaking feature designed for iPhone users to keep tabs on how their apps access personal data and engage with third-party services. This useful tool equips users with essential insights into app behavior, allowing them to make educated choices regarding their privacy. Here’s everything you need to know about utilizing the App Privacy Report to safeguard your information.
Understanding the App Privacy Report
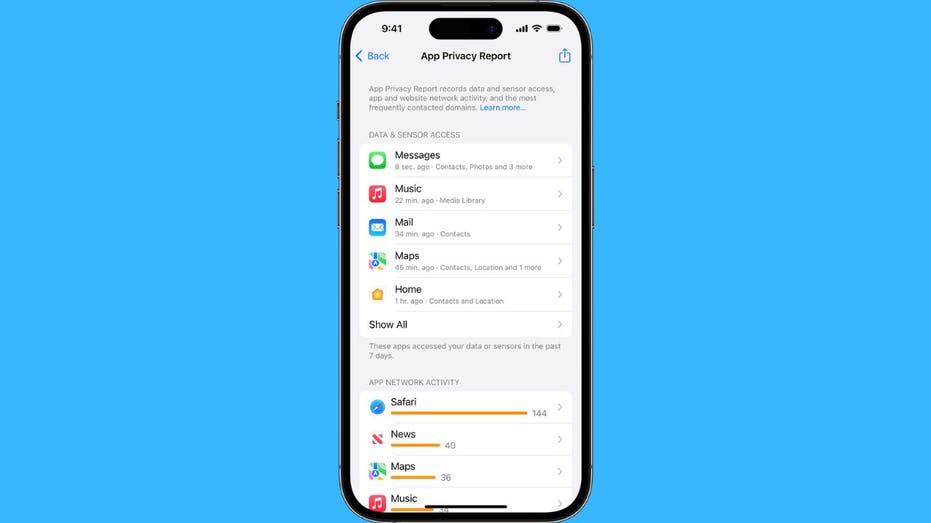
The App Privacy Report is an invaluable resource that breaks down app interactions with your data. To begin using this feature on your iPhone (currently on iOS 18.3.1), follow these straightforward steps:
1. Navigate to **Settings**.
2. Select **Privacy & Security**.
3. Tap on **App Privacy Report** to enable it.
Once activated, the report gathers data over a period of seven days, delivering a detailed overview of app activities.
Key Sections of the App Privacy Report
The App Privacy Report is organized into four main sections, each offering critical information about your app usage:
1. **Sensitive Data Access**: This section reveals which apps have accessed sensitive information, such as your location, contacts, photos, camera, and microphone. Pay special attention to apps that access data even when not actively in use, which could indicate potential privacy concerns.
2. **Network Traffic Overview**: Here, you can view the network traffic generated by apps and the connections they establish with external domains. This information is crucial for identifying if and how your data might be getting shared with third parties.
3. **Website Interaction Insights**: This part of the report displays the network activity of websites you visit within apps. It provides a clear picture of how your interactions are being tracked across different platforms.
4. **External Domain Connections**: This section details which external domains and websites your apps frequently interact with. Understanding these connections is particularly helpful for recognizing where your data may be sent after you leave an app.
Taking Action to Protect Your Privacy
After reviewing your App Privacy Report, there are several proactive steps you can take to enhance your digital privacy:
– **Limit Ad Tracking**: Consider adjusting your settings to restrict ad tracking by navigating to **Settings** > **Privacy & Security** > **Apple Advertising** and toggling off Personalized Ads.
– **Use Trusted Security Tools**: While Apple’s App Privacy Report is a great starting point, it doesn’t entirely prevent apps, websites, and data brokers from tracking your movements. Employing reliable security software can offer an added layer of protection against cyber threats, such as malware, phishing, and ransomware.
– **Consider a Personal Data Removal Service**: Your private information is often collected and sold by data brokers, making you susceptible to scams and identity theft. Although no service can guarantee the complete removal of your data from the internet, ongoing monitoring can help keep your information away from prying eyes.
Stay Informed and Engaged
The App Privacy Report is a powerful tool for iPhone users who are serious about their digital privacy. Regularly reviewing this report can help you better understand how apps manage your personal data and empower you to take the necessary actions to protect your privacy. While not every network connection suggests malicious intent, being informed enables you to make conscious decisions about the apps you use and the permissions you grant.
Have you discovered any surprising or concerning app behaviors in your App Privacy Report? We encourage you to share your experiences with us at Cyberguy.com/Contact.
For additional tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter at Cyberguy.com/Newsletter.
Follow Kurt on his social platforms for more insights, and feel free to ask questions or suggest topics for future coverage.
Copyright 2025 CyberGuy.com. All rights reserved.

